|
The WiFi Pineapple is a unique device developed by Hak5 for the
purpose of WiFi auditing and penetration testing. Since 2008 the
WiFi Pineapple has grown to encompass the best rogue access point
features, unique purpose-built hardware, intuitive web interfaces,
versatile deployment options, powerful software and hardware
development aids, a modular application ecosystem and a growing
community of passionate penetration testers.
ROBUST
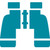
 The
WiFi Pineapple is the only hardware with dual integrated radios
custom built for advanced wireless attacks. The Mark V generation
is based on the formidable Atheros AR9331 system on a chip (SoC),
which includes a 400 MHz MIPS processor, 16 MB ROM and 64 MB RAM.
Onboard is the infamous Realtek RTL8187 radio with monitor and
injection capabilities, a Micro SD memory expansion port, a bank of
configurable auto-attack mode switches, a USB 2.0 host port and
10/100 Ethernet port. The
WiFi Pineapple is the only hardware with dual integrated radios
custom built for advanced wireless attacks. The Mark V generation
is based on the formidable Atheros AR9331 system on a chip (SoC),
which includes a 400 MHz MIPS processor, 16 MB ROM and 64 MB RAM.
Onboard is the infamous Realtek RTL8187 radio with monitor and
injection capabilities, a Micro SD memory expansion port, a bank of
configurable auto-attack mode switches, a USB 2.0 host port and
10/100 Ethernet port.
SIMPLE
At the core of the WiFi Pineapple is a modular web interface
designed to simplify the management and execution of advanced
attacks. A set of "infusions" (modules) provide convenient
graphical front-ends for popular command line applications.
Infusions can be installed to the device over-the-air from an
online portal. These free applications install in a matter of
clicks. Additionally, infusions may be developed directly on the
device using the open application programming interface (API). Once
submitted for review, your Infusion will be included in the online
portal for all WiFi Pineapple users.

INTELLIGENT
With the ability to perform passive reconnaissance of WiFi nodes
in proximity, the penetration tester is provided a visual
interpretation of the wireless landscape, complete with access
points, their connected clients, and unassociated clients. This
actionable intelligence provides the tester with the information
necessary to target specific networks or individuals.
INTEGRATED
The WiFi Pineapple integrates with standard pentest frameworks
such as Metasploit via Meterpreter. A standard toolset offers
popular utilities such as nmap, sslstrip, aircrack-ng, dsniff,
tcpdump and many more via downloadable packages or infusions.
Standard file formats such as pcap can be captured from the device
on to Micro SD cards for later analysis using tools such as
Wireshark and Kismet.
EFFECTIVE
Man-in-the-Middle power is achieved through PineAP. By
thoroughly mimicking Preferred Networks, this advanced Rogue Access
Point suite attracts modern smart devices into connecting to the
WiFi Pineapple. Capable of impersonating public and secured WiFi
access points, with its device specific precision, PineAP provides
the penetration tester with targeted client acquisition
capabilities. In this scenario the attacker can monitor all network
traffic flowing between an Internet gateway and the connected
clients as well as manipulate this data in transit such as through
captive portals, DNS spoofing, IP redirection and even the
substitution of executables in transit.

RECONNAISSANCE
Visualize WiFi landscape. Target networks and individuals.

AUTO HARVEST
Collect probe requests and beacons for rebroadcast.

DOGMA
Attract specific targets or all devices with thousands of
beacons.
 BEACON
RESPONSE BEACON
RESPONSE
Mimic networks with automatic targeted beacons.
 KARMA KARMA
Capture clients no matter what network they seek.
PERSISTENT
Deploy with confidence while maintaining persistence, pivoting,
and potential. Either through Meterpreter sessions, SSH shells or
SSL VPN tunnels, the WiFi Pineapple will keep a constant connection
to your home base for uninterrupted monitoring and management by
one user or an entire red team. Out-of-band connections may be
established as the WiFi Pineapple supports over 300 Mobile
Broadband modems and Android USB tethering.
VERSATILE
As a small form factor device with low energy requirements and
variable voltage acceptance from 5-12v, the WiFi Pineapple is
perfect for long duration stealth deployments. In many novel
enclosures, the WiFi Pineapple can be easily concealed at client
sites throughout an entire engagement. An accessible serial port
provides dedicated console access while the expansion bus may host
a Hardware Development Kit (HDK) module for custom projects. The
device firmware can be reset to defaults or reinstalled without
need for additional hardware by using a convenient DIP switch
configuration.
COMPLETE
The WiFi Pineapple Mark V provides incredible value. Included
with any kit is access to an active community support forum,
Pineapple University tutorial videos and documentation. Software
patches and firmware upgrades are provided free of charge
throughout the life of the device. Registering your product and
enjoy accessory discounts at the HakShop.
CREATIVE
Whether demonstrating vulnerabilities or discovering new ones,
the WiFi Pineapple is more than a platform - it's a community for
creativity. Rickrolling clients, powering off WiFi drones
mid-flight, tracking commercial airliners and logging
WiFi connections are only some of the creative things being
done within the WiFi Pineapple community. Your creativity is
welcomed on this Linux based embedded device with support for
python, php, perl and ruby. Why not join the community?
|

PURPOSE BUILT HARDWARE
The only purpose built WiFi pentest tool. Designed for advanced
rogue applications, monitoring and injection. The infamous AR9331
and RTL8187 join forces in “PineAP”.

MANIPULATE TRAFFIC
Spoof DNS, Split and Strip SSL, Redirect traffic to Captive
Portal harvesters. Replace binaries in transit. Inject
Javascript.

EXPANDABLE
Memory expansion by integrated Micro SD reader. Exposed UART for
convenient console access. HDK and BUS for Hardware Development.
USB - 4G Modems, Android Tethering, WiFi Adapters
|

REMOTE MANAGEMENT
For one user or an entire red team. Access from anywhere with
persistent reverse SSH shells, SSL VPN relays or pivot through a
meterpreter session in Metasploit.
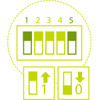
AUTO ATTACK SWITCHES
Mode switches deliver customized boot-time payloads without the
need to login. Simply flip the switches to your attack mode of
choice and power on.

SIMPLE WEB INTERFACE
An intuitive web interface simplifies even the most
advanced attacks. Easily visualize the WiFi landscape
and execute attacks.
|
|






















 BEACON
RESPONSE
BEACON
RESPONSE KARMA
KARMA